Read about CyText2.0 with superior features, including unlimited Private/Public Key support.
Download a copy of the freeware version: CyText1.0
CyText Encryption software for the masses.
* Encrypt your Chat Session Messages
* Share Secret Group Encryption Keys for Mutli-Way private chatting within a public forum.
* Keep your Email messages from prying eyes, as well as any other text.
Read about CyText2.0 with superior features, including unlimited Private/Public Key support. Download a copy of the freeware version: CyText1.0 |
 |
Product Features
CyText-1
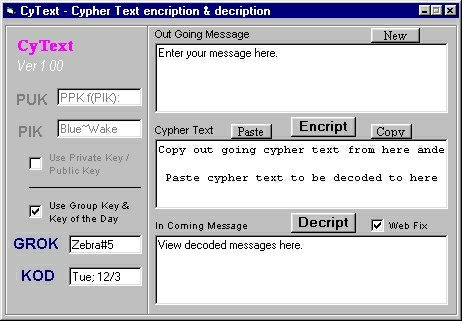
CyText is a fast and simple to use text encryption / decryption application. CyText1 uses two keys for added security and flexibility of use. The idea is that one key (the Group Key, GROK) you agree upon and share among a group; while the second key (the Key of the Day, KOD) is changed more readily, perhaps daily, or can be set for exchanging messages with one specific person. The algorithm it uses is symmetric, meaning you must use the exact same keys to decrypt as were used to encrypt a message. All of the messages can easily be copied and pasted to and from other applications, such as email or chat rooms.
CyText-1 can handle messages using the ASCII printable
character set. A poly-alphabetic substitution algorithm with
additional steps taken to prevent cryptanalysis by character
frequency analysis is utilized. This means that encrypted
messages are safe from attack by non-professionals.
For unbreakable protection from serious and truly professional
cryptanalytsts (code breakers) pay your dues and get CyText-2.
CyText-2 has both added features and security. CyText-2's basic algorithm is far more secure than that of CyText-1. The original message is scrambled prior to the application of nearly unlimited poly-alphabets. With CyText-2 there is an inter-dependent multi-dimensional relationship between components of the original and cipher text. It would require no less than a professional world class cryptanalyst to even stand a chance to break a message encrypted with CyText-2; and then it would take years with the help of super-computers.
CyText-2 offers a form of Private / Public Key (PPK) cryptography, which is a proprietary innovation based on the works of Diffie, Hellman & Merkle. CyText-2 will generate, on the fly at no extra charge unlimited Pulic/Private key pairs. There is no PPK key management infrastructure to deal with. This process involves very large primes with special characteristics and calculations with more than 64 bits (& intermediate calculations may exceed 128 bits). Hence the operations can not be done directly with a 64 bit CPU instruction set. This also is why it takes about 2 seconds (on a 700Mhz PC) to generate a Private key to match a given Public key. If the few seconds it will take for encryption and description is undesirable then the PPK algorithm can simply be used to securely exchange keys to be used with the normal symmetric CyText-2 algorithm; making it just as secure, and perhaps arguably even more so.
CyText-2 additional features:
How to get your own copy of CyText2.0
| Site Home | email: Site Administrator | RonMiller ©2000